Ero sivun ”RouterOS Firewall/en” versioiden välillä
(Ak: Uusi sivu: With filter rules you can limit the transmission of packages to the router or through the router. Note, that in the RouterOS operating system firewall rules are created from the to...) |
(Ak: Uusi sivu: == Sources ==) |
||
| (16 välissä olevaa versiota samalta käyttäjältä ei näytetä) | |||
| Rivi 17: | Rivi 17: | ||
With filter rules you can limit the transmission of packages to the router or through the router. Note, that in the RouterOS operating system firewall rules are created from the top down. | With filter rules you can limit the transmission of packages to the router or through the router. Note, that in the RouterOS operating system firewall rules are created from the top down. | ||
| − | === | + | === Basic firewall === |
| − | + | In our example we create a secure and basic RouterOS firewall which suits the needs of all basic users. | |
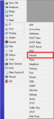
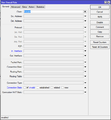
| − | + | First we create a new allow rule, which always allows connecting to the router from whatever network and with whatever protocol. You should do this in order to not accidentally lock yourself outside of the router while you work. | |
/ip firewall filter add chain=input action=accept | /ip firewall filter add chain=input action=accept | ||
| Rivi 30: | Rivi 30: | ||
</gallery> | </gallery> | ||
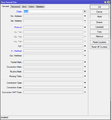
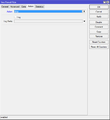
| − | + | We create a second firewall rule which allows traffic through the router. The connection must be trusted though. | |
/ip firewall filter add chain=forward connection-state=established,related action=accept | /ip firewall filter add chain=forward connection-state=established,related action=accept | ||
| Rivi 39: | Rivi 39: | ||
</gallery> | </gallery> | ||
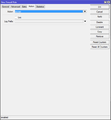
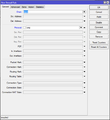
| − | + | We block invalid connections from going through the router. | |
/ip firewall filter add chain=forward connection-state=invalid action=drop | /ip firewall filter add chain=forward connection-state=invalid action=drop | ||
| Rivi 48: | Rivi 48: | ||
</gallery> | </gallery> | ||
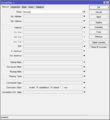
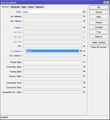
| − | + | Next we select the ICMP protocol, the so called ''ping'' protocol. This allows the routed to be pinged with a client device, which is connected to the Mikrotik. Useful for troubleshooting. | |
/ip firewall filter add chain=input protocol=icmp action=accept | /ip firewall filter add chain=input protocol=icmp action=accept | ||
| Rivi 57: | Rivi 57: | ||
</gallery> | </gallery> | ||
| − | + | Next we create a rule which blocks incoming traffic from the ether1 (WAN) port. | |
/ip firewall filter add chain=input in-interface=ether1 action=drop | /ip firewall filter add chain=input in-interface=ether1 action=drop | ||
| Rivi 66: | Rivi 66: | ||
</gallery> | </gallery> | ||
| − | + | Now we have the basic firewall configurations set up. The firewall works from the top to down (0 ->) along the list. By default everything is allowed unless otherwise is mentioned. | |
/ip firewall filter print | /ip firewall filter print | ||
| Rivi 74: | Rivi 74: | ||
</gallery> | </gallery> | ||
| − | === | + | === Block outside access to the management ports === |
| − | + | We block outside network access to the management ports, 21, 22, 23 and 80. An attacker would first have to access your internal network to access the router. | |
/ip firewall filter add chain=input protocol=tcp dst-port=21,22,23,80 in-interface=ether1 action=drop | /ip firewall filter add chain=input protocol=tcp dst-port=21,22,23,80 in-interface=ether1 action=drop | ||
| Rivi 82: | Rivi 82: | ||
== NAT == | == NAT == | ||
| − | + | We have a separate article on [[RouterOS NAT]]. | |
== Mangle == | == Mangle == | ||
| − | Mangle | + | With Mangle you can mark different packets with different signs. You can tag some packets with the mark and use them for instance in [[RouterOS Queue]], NAT and routing. Mangle's marks are just the router's own marks so they aren't transferred forward across the network in the packets. |
=== Marking Packets === | === Marking Packets === | ||
| − | + | We mark, for instance the packets going through the interface ether1-gateway port 80. | |
/ip firewall mangle add chain=forward protocol=tcp dst-port=80 in-interface=ether1-gateway action=mark-packet new-packet-mark=HTTP | /ip firewall mangle add chain=forward protocol=tcp dst-port=80 in-interface=ether1-gateway action=mark-packet new-packet-mark=HTTP | ||
| Rivi 99: | Rivi 99: | ||
</gallery> | </gallery> | ||
| − | == | + | == Related info == |
* [[RouterOS Queue]] | * [[RouterOS Queue]] | ||
* [[RouterOS NAT]] | * [[RouterOS NAT]] | ||
| − | == | + | == Sources == |
http://wiki.mikrotik.com/wiki/Manual:IP/Firewall/Filter | http://wiki.mikrotik.com/wiki/Manual:IP/Firewall/Filter | ||
Nykyinen versio 21. elokuuta 2015 kello 07.25
With the firewall we can filter packages and enable other kinds of security options, which either block or allow access to the network / router. Used in unison with a NAT, this significantly helps in blocking unauthorized outside access to your internal network.
RouterOS firewall mainly follows the same logic as Linux when it comes to Iptables.
Firewall settings are in the RouterOS system:
/ip firewall
Sisällysluettelo
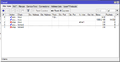
Filter Rules
With filter rules you can limit the transmission of packages to the router or through the router. Note, that in the RouterOS operating system firewall rules are created from the top down.
Basic firewall
In our example we create a secure and basic RouterOS firewall which suits the needs of all basic users.
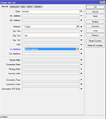
First we create a new allow rule, which always allows connecting to the router from whatever network and with whatever protocol. You should do this in order to not accidentally lock yourself outside of the router while you work.
/ip firewall filter add chain=input action=accept
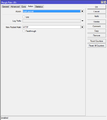
We create a second firewall rule which allows traffic through the router. The connection must be trusted though.
/ip firewall filter add chain=forward connection-state=established,related action=accept
We block invalid connections from going through the router.
/ip firewall filter add chain=forward connection-state=invalid action=drop
Next we select the ICMP protocol, the so called ping protocol. This allows the routed to be pinged with a client device, which is connected to the Mikrotik. Useful for troubleshooting.
/ip firewall filter add chain=input protocol=icmp action=accept
Next we create a rule which blocks incoming traffic from the ether1 (WAN) port.
/ip firewall filter add chain=input in-interface=ether1 action=drop
Now we have the basic firewall configurations set up. The firewall works from the top to down (0 ->) along the list. By default everything is allowed unless otherwise is mentioned.
/ip firewall filter print
Block outside access to the management ports
We block outside network access to the management ports, 21, 22, 23 and 80. An attacker would first have to access your internal network to access the router.
/ip firewall filter add chain=input protocol=tcp dst-port=21,22,23,80 in-interface=ether1 action=drop
NAT
We have a separate article on RouterOS NAT.
Mangle
With Mangle you can mark different packets with different signs. You can tag some packets with the mark and use them for instance in RouterOS Queue, NAT and routing. Mangle's marks are just the router's own marks so they aren't transferred forward across the network in the packets.
Marking Packets
We mark, for instance the packets going through the interface ether1-gateway port 80.
/ip firewall mangle add chain=forward protocol=tcp dst-port=80 in-interface=ether1-gateway action=mark-packet new-packet-mark=HTTP
Related info
Sources
http://wiki.mikrotik.com/wiki/Manual:IP/Firewall/Filter http://wiki.mikrotik.com/wiki/Manual:IP/Firewall/Mangle