Cisco IOS basic usage
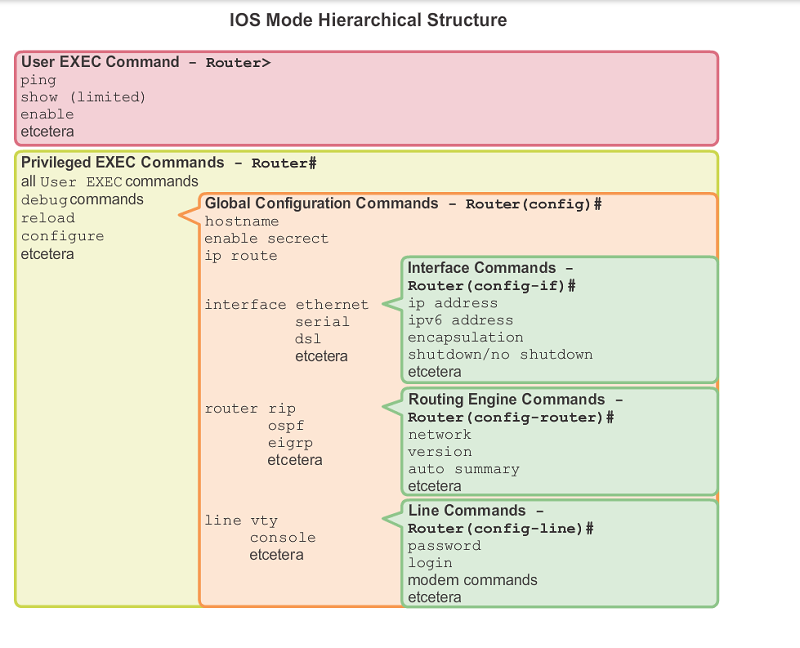
Cisco IOS is found on nearly every Cisco router and switch. They both use a hierarchical structure.
Sisällysluettelo
Basic use
In Cisco IOS you can always get more information and help with a command by putting ? after the comand. Think of it as man in Linux, just in the end. For instance, the next command prints all commands that are available in the User mode.
Switch> ?
Using the Tab key you can quicktype commands or get suggestions for commands, just like Linux. In Cisco IOS you can also use shortened words to avoid typing long commands. In order to use shortened commands, you must type the command far enough that there is no other command that starts with the letters you typed than just one. In the next example we run the command copy running-config startup-config
copy start run
The command line is ready when you see this mark below:
<cr>
When your command is missing parameters or information you will be presented with the following error. In this case use ? or tab to find out how to properly run the command.
% Incomplete command
The command is incorrect or has a typo:
% Invalid input detected at '^' marker
Exit / Close
exit
User mode
The switch/router normally boots straight into user mode. In this state you can't really do much anything, so we transition into the Privilege mode.
In this state you can for example ping addresses and show some limited info.
Switch> ping 8.8.8.8
Privilege state
You can get into privilege state using the command
Switch> enable
The switch/router will prompt for a password if one has been set up.
In the privilege state you can browse the current configuration
Switch# show running-config
As well as current VLANs
Switch# show vlan
You can also copy the running configuration to the startup configuration, as if to "save" your configuration. It's recommended to do this quite often as configuring a switch for an hour only to lose power and have your progress wiped is VERY annoying.
Switch# copy running-config startup-config
You can also save the config with the following command (also works in HP network equipment)
Switch# write memory
Remove configurations
Switch# erase startup-config
And restart.
Show network adapters
Switch# show interface
Show IP-addresses
Switch# show ip interface
Show routing (Layer 3 switch and router)
Router# show ip route
Show ARP table
Switch# show arp
Show firmware version
Switch# show version
Backing up and returning the configuration
When backing up configurations you will need a TFP server.
Using TFTP, copy the startup configuration from the network device to your PC. You can also copy the configurations into a .txt file when you print using the show running-config command. Simply copypaste.
copy startup-config tftp
After this you will be asked:
- For a host name or IP address to the TFTP server
- Filename of the to be saved configuration file
- Confirm save
return config from TFTP
copy tftp running-config
- Host name or IP address to TFTP server
- Filename from which the configuration is restored
- Confirm restore
Save running-config to the startup config if you want the returned configuration to be loaded when the device boots.
Configure mode
You can get to the configure mode using the command
Switch# configure terminal
In the configure mode you make the configurations for the switch (No shit sherlock!).
Passwords
Protect the switch by setting passwords.
Console connection
We recommend to set a password for the console port connection
Switch(config)# console 0
password passwordhere
login
Telnet
Using a telnet connection you can configure the switch/router without being connected using a console cable. Telnet connections are disabled by default. Before using telnet you must set an IP address for the switch.
Switch(config)# line vty 0 [1-15]
0-15 defines how many simultaneous connections are allowed. 0 = 1 connection, 1 = 2 connections etc.
It is highly recommended to protect telnet connections with a password, because otherwise anybody can access the switch and it's configurations without even physical access to the device itself.
password passwordhere
And enable logging in
login
Enable password
Switch(config)# enable password passwordhere (this method is not recommended!)
Switch(config)# enable secret passwordhere (this is the recommended method)
Now you must give a password when switching to enable mode.
Encrypt all passwords
This will encrypt all the passwords used on the device so they won't be shown in plain text when running the show running-config command.
Switch(config)# service password-encryption
Banners
The banner is shown before logging in.
Switch(config)# banner motd #This is secure system! Authorized Access ONLY!!!!#
Interface
All connections are connected using switches, so all connections are defined using the interface command.
Switch the settings of one port in the switch:
Switch(config)# interface FastEthernet 0/1
Switch(config)# interface GigabitEthernet 1/1
Switch the settings of multiple ports in the switch:
Switch(config)# interface range FastEthernet 0/1 - 20
Switch(config)# interface GigabitEthernet 1/1 - 2
Description
You can give a description for the network connection
Switch(config)# interface FastEthernet 0/1
description connection to Admin LAN
exit
Example description was a notification of connecting to the administrator network.
IP address
Select your interface or interface range (such as FastEthernet 0/1)
Switch(config)# interface FastEthernet 0/1
ip address 10.0.0.1 255.255.255.0
exit
VLAN
We define the interface or interfaces for a certain VLAN, for instance VLAN2. By default all interfaces are in VLAN1.
Switch(config)# interface FastEthernet 0/1
swicthport mode access
switchport access vlan 2
exit
Now interface FastEthernet 0/1 is in VLAN 2 and other interfaces in VLAN 1.
VLAN
By default a switch only has one VLAN (VLAN1).
We define the IP address and subnet mask for VLAN1.
Switch(config)# interface vlan 1
ip address 10.10.10.100 255.255.255.0
no shutdown
Now we have defined VLAN1 to have the IP address 10.10.10.100 and subnet mask 255.255.255.0
By default all ports are in VLAN1.
We add a new VLAN
Switch(config)# interface vlan 2
ip address 192.168.1.200 255.255.255.0
no shutdown
We define certain ports to be in VLAN1 and some in VLAN2. For instance, FastEthernet 1-12 to be in VLAN1 and FastEthernet 13-24 to be in VLAN2.
Switch(config)# interface range fastethernet 0/1 - 2
switchport mode access
switchport access vlan 1
interface range fastethernet 0/13 - 24
switchport mode access
switchport access vlan 2
Port Security
Port protection can be done in three different ways: Static, Dynamic and Sticky.
For static protection you define one MAC address for the connection. Only a device with that MAC address can use the port.
Dynamic protection works using a MAC table.
Sticky remembers the defined amount of MAC addresses, which are allowed to use the port.
Static Port Security
First we select the port or port range
Switch(config)# interface fastEthernet 0/11
We go into access mode. You can't make port security configurations in default mode.
Switch(config)# switchport mode access
We enable port prtoection
Switch(config)# switchport port-security mac-address mac-address [vlan {vlan-id | {access | voice}]
Dynamic Port Security
First we select the port or port range
Switch(config)# interface fastEthernet 0/11
We go into access mode. You can't make port security configurations in default mode.
Switch(config)# switchport mode access
We enable port prtoection
Switch(config)# switchport port-security
Sticky Port Security
First we select the port or port range
Switch(config)# interface fastEthernet 0/11
We go into access mode. You can't make port security configurations in default mode.
Switch(config)# switchport mode access
We enable port prtoection
Switch(config)# switchport port-security
We define the desired maximum amount of safe addresses
Switch(config)# switchport port-security maximum 50
We enable Sticky learning
Switch(config)# switchport port-security mac-address sticky