Ero sivun ”RouterOS OpenVPN/en” versioiden välillä
(Ak: Uusi sivu: * name = connection name * connect-to = OpenVPN Server address or IP-address * port = OpenVPN Server port what server listen * mode = ip (ethernet, if you use bridge mode on VPN se...) |
(Ak: Uusi sivu: 3. Try connect and watch log if connection not working.) |
||
| Rivi 120: | Rivi 120: | ||
* add-default-route = Add this VPN to default route? | * add-default-route = Add this VPN to default route? | ||
| − | 3. | + | 3. Try connect and watch log if connection not working. |
=== Linux === | === Linux === | ||
Nykyinen versio 17. elokuuta 2016 kello 21.22
RouterOS support OpenVPN server and client. OpenVPN is one mostly secure VPN tunnel protocol.
Sisällysluettelo
Server
This manual shows, how to configure Mikrotik OpenVPN Server.
Requirements / Recommendation =
- SSL Root Certificate (CA)
- SSL Server Certificate
- SSL Client Certificate
- Tested Mikrotik RB951G-2HnD and RouterOS 6.26
How to
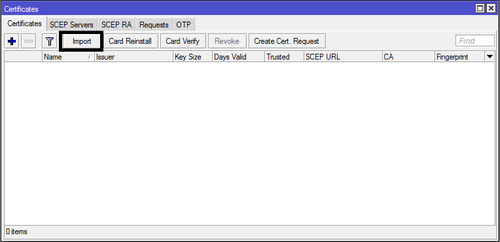
1. Create SSL certificate first, example OpenSSL and move certificate to Mikrotik with Winbox.
Import Certificate key and certificate to RouterOS.
/certificates import file-name=ssl.key
/certificates import file-name=ssl.crt
2. Create DHCP Pool (if you want use bridge, you can skip this step)
/ip pool add name=ovpn-pool ranges=10.15.32.34-10.15.32.38
- DHCP pool name is ovpn-pool
- Pool area is 10.15.32.34-10.15.32.38
3. Create routing OpenVPN network to local network (if you want use bridge mode, you can skip this step)
/ip firewall nat add chain=srcnat out-interface=ether2 action=masquerade
Create NAT to ether2 interface
4. Create OpenVPN Profile
/ppp profile add name=openvpn local-address=10.15.32.33 remote-address=ovpn-pool
- Profile name is openvpn
- Local IP-address is 10.15.32.33
- VPN customer get remote IP-address from ovpn - DHCP pool.
- Using bridge, please remove local-address and remote address. Add bridge, example bridge-local
/ppp profile add name=openvpn_bridge bridge=bridge-local
5. Create VPN user
/ppp secret add disabled=no name="openvpn" password="Qwerty1" service=any
- Username: openvpn
- Password: Qwerty1
- Service what can use this user: Openvpn
6. OpenVPN server configuration
/interface ovpn-server server set auth=sha1, certificate=ssl_cert cipher=aes128,aes256 default-profile=openvpn enabled=yes keepalive-timeout=60 max-mtu=1500 mode=ip netmask=29 port=1194 require client-certificate=no
- Authentication: SHA1
- SS Certificate: ssl-cert
- SSL Chipper: AES128, AES256
- Default Profile: openvpn
- Keepalive-timeout=60
- MAX-MTU (packet size): 1500
- mode=ip (if you use bridge mode, change this to ethernet)
- require client-certificate=no (if you use client certificate, change value to yes)
6. Enable access from firewall
/ip firewall filter add action=accept chain=input comment="OpenVPN" disabled=no dst-port=1194 protocol=tcp
Create new firewall rule what accept protocol TCP port 1194
Radius
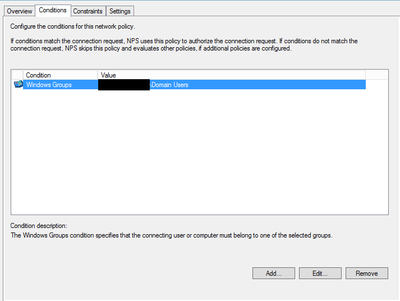
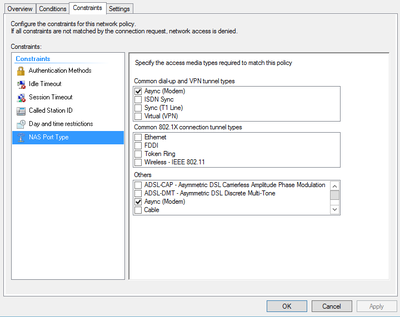
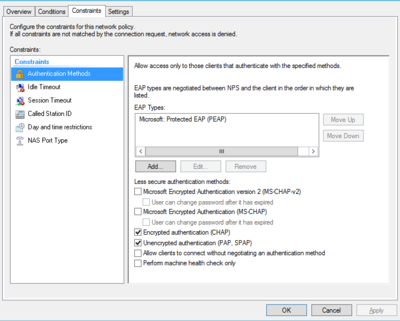
- Lisää Mikrotikkiin Radius palvelimesi asetukset /radius alle.
- Määritä palvelimelle sallituksi todennustyypit CHAP / PAP, SPAP
- Määritä NAS Port tyypiksi Async.
/radius add service=ppp address=10.0.0.254 secret=securepassu authentication-port=1812 accounting-port=1813
Esimerkki konfiguraatiot Windows NPS palvelimelta.
Client
RouterOS
OpenVPN client can connect to OpenVPN server.
1. Create OpenVPN client profile to client device.
/ppp profile add name=openvpn-client
2. Create new OpenVPN client:
/interface ovpn-client name="openvpn-client" connect-to="server.openvpn.com" port="1194" mode="ip" user="openvpn" password="openvpn123" profile="openvpn-client" certificate="no" auth="sha1" cipher="aes128" add-default-route="no"
- name = connection name
- connect-to = OpenVPN Server address or IP-address
- port = OpenVPN Server port what server listen
- mode = ip (ethernet, if you use bridge mode on VPN server)
- user = OpenVPN user
- password = OpenVPN user password
- profile = Profile what OpenVPN use
- certificate = SSL client certificate
- add-default-route = Add this VPN to default route?
3. Try connect and watch log if connection not working.
Linux
Esimerkki konfiguraatio client.ovpn:
client dev tun #Voi olla tap. Tun on reitittävä ja tap on siltaava. Katso että vastaa palvelimen konfiguraatiota. proto tcp #Tai udp, RouterOS ei tue UDP:nä. resolv-retry infinite nobind remote vpn.example.org 1194 # Etä OpenVPN palvelimen osoite tai IP-osoite sekä portti #Lisää tähän rootCA jonka olet luonut, avaa se ja kopioi sisältö <ca> -----BEGIN CERTIFICATE----- -----END CERTIFICATE----- </ca> #Lisää tähän asiakas sertifikaatin jonka olet luonut. <cert> -----BEGIN CERTIFICATE----- -----END CERTIFICATE----- </cert> #Lisää tähän asiakkaan sertifikaatin privaatti avaimen. <key> -----BEGIN PRIVATE KEY----- -----END PRIVATE KEY----- </key> tls-client port 1194 #Portti jota palvelin kuuntelee user nobody group nogroup #comp-lzo # Do not use compression. It doesn't work with RouterOS (at least up to RouterOS 3.0rc9) # More reliable detection when a system loses its connection. ping 15 ping-restart 10 ping-timer-rem persist-tun persist-key # Silence the output of replay warnings, which are a common false # alarm on WiFi networks. This option preserves the security of # the replay protection code without the verbosity associated with # warnings about duplicate packets. mute-replay-warnings # Verbosity level. # 0 = quiet, 1 = mostly quiet, 3 = medium output, 9 = verbose verb 3 cipher AES-256-CBC auth SHA1 pull route-nopull #Verkot jotka reititetään VPN verkkoon route 192.168.1.0 255.255.255.0 push "dhcp-option DNS 8.8.8.8" #DNS palvelin jota käytetään #redirect-gateway def1 #Haluatko reitittää kaikki VPN kautta? Ota tästä risuaita pois #Salasana tiedosto auth-user-pass auth.cfg
auth.cfg tiedoston tulisi sisältää käyttäjänimen (username) ja salasananan (password)
username password