Ero sivun ”IPsec/en” versioiden välillä
(Ak: Uusi sivu: We enable aaa new-model simply by running the command aaa new-model) |
(Ak: Uusi sivu: And we're in.) |
||
| (14 välissä olevaa versiota samalta käyttäjältä ei näytetä) | |||
| Rivi 29: | Rivi 29: | ||
aaa new-model | aaa new-model | ||
| − | + | We aren't talking about an AA-club, AAA stand for authentication-authorization-accounting. It is often used when fiddling with authentication and the likes. | |
| − | + | Now we define logins to be locally sourced and not for instance from a radius server. | |
| − | + | aaa authentication login IPsecE local | |
| − | + | aaa authorization network IPsecO local | |
| − | + | We tell the router to ALWAYS use esp-3des esp-md5-hmac encryption. | |
| − | + | crypto ipsec transform-set Example esp-3des esp-md5-hmac | |
| − | + | We create a dynamic field which makes ipsec use example encryption. | |
| − | + | crypto dynamic-map TestMap 7 | |
| − | set transform-set | + | set transform-set Example |
| − | + | We make a isakmp policy which defines the connection's tweaks: | |
| − | + | crypto isakmp policy 7 | |
encr 3des | encr 3des | ||
authentication pre-share | authentication pre-share | ||
group 2 | group 2 | ||
| − | + | Then we create a group for ipsec | |
| − | + | crypto isakmp client configuration group Testers | |
| − | key | + | key Key |
| − | pool | + | pool testpool |
netmask 255.255.255.0 | netmask 255.255.255.0 | ||
| − | + | We make an address space by the name testpool which gives addresses to clients. | |
| − | + | ip local pool testpool 192.168.70.20 192.168.70.30 | |
| − | + | Again we make a map and inspect the work we have done. | |
| − | + | crypto map ipsecmap client authentication list IpsecE | |
| − | + | crypto map ipsecmap isakmp authorization list IpsecO | |
| − | + | crypto map ipsecmap client configuration address respond | |
| − | + | crypto map ipsecmap 7 ipsec-isakmp dynamic TestMap | |
| − | NAT | + | We still need to setup NAT: |
| − | + | ip access-list extended nonat | |
deny ip 192.168.100.0 0.0.0.255 192.168.70.0 0.0.0.255 | deny ip 192.168.100.0 0.0.0.255 192.168.70.0 0.0.0.255 | ||
permit ip any any | permit ip any any | ||
| Rivi 71: | Rivi 71: | ||
| − | + | We still make a user. | |
| − | + | username johannes password 0 Qwerty1 | |
| − | + | Now we test our VPN | |
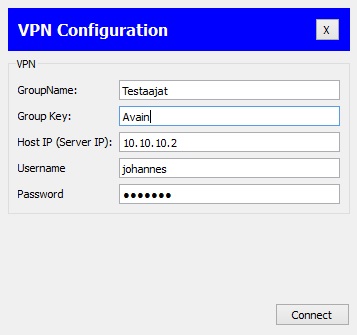
| − | + | We put the information in their place. The picture has the credentials from the original Finnish manual but you can just substitute them with the ones from this manual's configuration which we did above. Testers / Key / 10.10.10.2 / johannes / Qwerty1 | |
[[Tiedosto:Vpn1.jpg]] | [[Tiedosto:Vpn1.jpg]] | ||
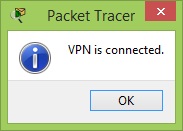
| − | + | And we're in. | |
[[Tiedosto:Vpn2.jpg]] | [[Tiedosto:Vpn2.jpg]] | ||
Nykyinen versio 27. elokuuta 2015 kello 07.02
{{#allow-groups:user}}
We make a cisco 2811 router into an ipsec host.
General info
WAN interface: fa0/0
LAN interface: fa0/1
Configuring
First we setup our network connections
interface FastEthernet0/0 description *allworkandnoplaymakestranslatoradullboy* ip address 10.10.10.2 255.255.255.0 ip nat outside ipv6 ospf cost 1 crypto map ipsecmap
interface FastEthernet0/1 description *areallydullboy* ip address 192.168.100.1 255.255.255.0 ip nat inside
We enable aaa new-model simply by running the command
aaa new-model
We aren't talking about an AA-club, AAA stand for authentication-authorization-accounting. It is often used when fiddling with authentication and the likes.
Now we define logins to be locally sourced and not for instance from a radius server.
aaa authentication login IPsecE local aaa authorization network IPsecO local
We tell the router to ALWAYS use esp-3des esp-md5-hmac encryption.
crypto ipsec transform-set Example esp-3des esp-md5-hmac
We create a dynamic field which makes ipsec use example encryption.
crypto dynamic-map TestMap 7 set transform-set Example
We make a isakmp policy which defines the connection's tweaks:
crypto isakmp policy 7 encr 3des authentication pre-share group 2
Then we create a group for ipsec
crypto isakmp client configuration group Testers key Key pool testpool netmask 255.255.255.0
We make an address space by the name testpool which gives addresses to clients.
ip local pool testpool 192.168.70.20 192.168.70.30
Again we make a map and inspect the work we have done.
crypto map ipsecmap client authentication list IpsecE crypto map ipsecmap isakmp authorization list IpsecO crypto map ipsecmap client configuration address respond crypto map ipsecmap 7 ipsec-isakmp dynamic TestMap
We still need to setup NAT:
ip access-list extended nonat deny ip 192.168.100.0 0.0.0.255 192.168.70.0 0.0.0.255 permit ip any any
ip nat inside source list nonat interface FastEthernet0/0 overload
We still make a user.
username johannes password 0 Qwerty1
Now we test our VPN
We put the information in their place. The picture has the credentials from the original Finnish manual but you can just substitute them with the ones from this manual's configuration which we did above. Testers / Key / 10.10.10.2 / johannes / Qwerty1
And we're in.